Single Sign-On (SSO): Seamless Authentication for Enterprise and Client Services
In this article, we will explain what SSO is and where it is used. We will also look at a technical implementation example for web applications.
Introduction
Single sign-on (SSO) is a technology that allows users to access all required services with a single set of credentials.
To better understand how SSO works, let’s look at a couple of examples:
Examples of SSO
In an Enterprise Environment
Imagine you work for a company that uses various applications, such as an email client, task tracker, and corporate messenger. Each application requires user authentication. Without SSO, users must enter their login and password for each application. Moreover, for information security purposes, these passwords must be different, so that if one is leaked, attackers cannot access all services with the leaked credentials.
With SSO, however, an employee only needs to log in once to the operating system. After that, they do not need to authenticate again to use corporate applications, as they are use the account they logged in with. Of course, authentication and access authorisation for each service is performed, but this happens completely unnoticed by the user.
External Client Services
Another example is client services. Let’s say you are a customer of a company that provides several services. For example, the company might offer grocery delivery, an online movie theater, and a bank application. Before SSO, you had to log into each service separately, even though they belonged to the same organization. With SSO, you only need to log in once, and it doesn’t matter which application you’re using, whether it’s for banking or grocery delivery. After you log into one service, you’re automatically logged into any other service in the company.
Examples of Technical Implementation
Let’s take a look at an example of SSO implementation using one organization’s web applications as an example.
An example architecture is shown in the figure below
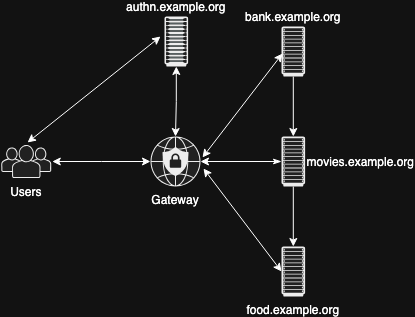
SSO consists of two components - an authentication service and an authorization gateway.
The gateway is set up in front of services that are used in the example.org domain.
Example user authentication scenario:
- A user attempts to log in to the bank application
- The gateway denies access and redirects the user to the authentication service
- The user enters their credentials into the service and is successfully authenticated
- The authentication service redirects the user back to the bank application
- The gateway verifies that the user is authenticated and allows the user into the bank application
- The user tries to log in to the online movie theater of the same company.
- The gateway sees that the user is already authenticated, and if the authentication session is valid, the user immediately logs into the online cinema with the same credentials he or she used in the banking application.
Another implementation is authentication using the Kerberos protocol. This approach is used within a corporate network. With Kerberos, users can access the corporate applications using their domain account, as described in the example above.
If the enterprise applications do not support Kerberos authentication, the SSO service can authenticate the users itself and pass the user’s session information to these applications through the authorization gateway.
Key Benefits
- Improved User Experience (UX): users do not need to re-authenticate when using apps, and do not need to remember their credentials for each application
- Security:
- Monitoring: by using a centralized authentication service, you can track user behavior and detect suspicious activity
- authorization: authorization policies for all services are configured in one place for easy management
- operative response: when suspicious activity is detected, you can request an additional authentication factor or revoke a suspicious session for all services at once.
- centralized account storage: allows you to block or grant additional access to certain groups of users (e.g. VIP clients) in one place.
Conclusion
Implementing Single Sign-On is a significant step toward simplifying the user experience and enhancing security. SSO minimizes the inconvenience of multiple authentications and provides companies with tools for centralized access management. SSO helps to create a seamless and secure experience when interacting with client or enterprise applications. With the increasing number of digital services, implementing SSO is becoming not just a convenience but a necessity for organizations.